Set Up Tunneling
IPv6 Tunneling
We assume that you have an OpenLBR running Debian. If not, go back to OpenLbr.
Goal
The goal of the following steps is to show you how to connect your OpenLBR onto the IPv6 Internet. Once that is working, OpenVirtualInterface shows you how to connect your LBR mote onto the OpenLBR, and onto the Internet. Our goal for now is to have both the OpenLBR and the Internet host inside the IPv6 cloud, and to be able to ping back and forth between them.
Setting up a single tunnel
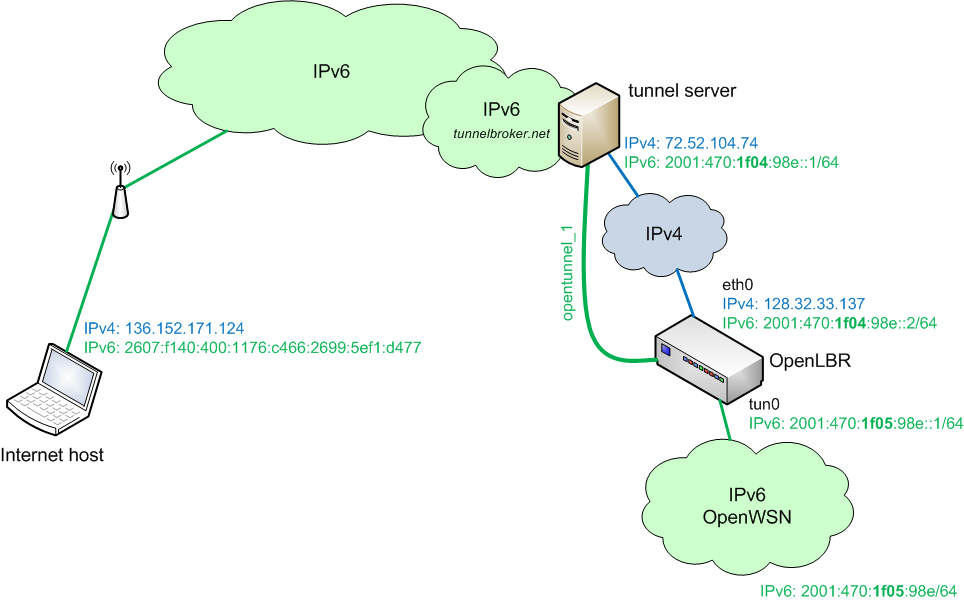
We use the topology depicted above. We assume that you have a Linksys NSLU2 'Slug' running Debian (as described in OpenLbr; we call it OpenLBR from now on), and an Internet host which is already connected to the IPv6 cloud. If that is not the case, you can build the multi-tunnel topology described in the sections below.
Note that we have populated the topology above with our IPv4/IPv6 address. You will have to change those to your own, obviously.
Testing connectivity in IPv4 world
Start your Internet host and OpenLBR, and connect them to the Internet.
Tip: use http://ip4.me/ to check your public IPv4 address.
From the Internet host:
# ping 136.152.171.124 (to itself) # ping 72.52.104.74 (to the tunnel server) # ping 128.32.33.137 (to the OpenLbr)
From the OpenLBR
# ping 128.32.33.137 (to itself) # ping 72.52.104.74 (to the tunnel server) # ping 136.152.171.124 (to the Internet host, this may fail*)
- Note that the last command may fail because your standard Windows distribution does not answer ping (ICMPv6 echo request) commands. If you start Wireshark (http://www.wireshark.org/) on the Internet host, you should see the Echo (ping) requests being sent from 128.32.33.137 but no reply. You can issue the following command to force Windows (Vista in this case) to reply to ping (you need to open a Command Prompt by right clicking and choosing Open as Administrator):
# netsh firewall set icmpsetting 8 enable
(remember, do not proceed as long as you don't 100% success on all of the above commands)
Register your tunnel
Tunnel broker is a free service created by Internet enthusiasts wishing to promote the use of IPv6. Their service allows you to set up a tunnel to connect your computer to the IPv6 cloud, through an IPv4 network.
- create an account in http://tunnelbroker.net/
- create a 'regular tunnel' once logged in
- when asked to enter the Client IPv4 address, enter the IPv4 address of the OpenLBR, in my case 128.32.33.137.
Setting up the tunnel from the LBR
At the bottom of your tunnel details page, choose "Linux-route2" in the drop-down and click Show Config. Enter the commands into your OpenLBR. In my case, I enter:
# modprobe ipv6 # ip tunnel add opentunnel_1 mode sit remote 72.52.104.74 local 128.32.33.137 ttl 255 # ip link set opentunnel_1 up # ip addr add 2001:470:1f04:98e::2/64 dev opentunnel_1 # ip route add ::/0 dev opentunnel_1 # ip -f inet6 addr
On the OpenLBR, you can then type ifconfig. The opentunnel_1 "virtual" interface should have been created:
opentunnel_1 Link encap:IPv6-in-IPv4
inet6 addr: 2001:470:1f04:98e::2/64 Scope:Global
inet6 addr: fe80::8020:2189/128 Scope:Link
UP POINTOPOINT RUNNING NOARP MTU:1480 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
Testing connectivity in IPv6 world
Tip: use http://ip6.me/ to check your public IPv6 address of the Internet host.
Note that, to force the use of IPv6 when issuing a ping, you use ping6 in Linux and ping -6 in Windows.
From the (Linux based) OpenLBR
# ping6 2001:470:1f04:98e::2 (to itself) # ping6 2001:470:1f04:98e::1 (to the tunnel server) # ping6 2607:f140:400:1176:c466:2699:5ef1:d477 (to the Internet host*)
- This will only work if you forced Windows on the Internet host to issue echo replies. See above.
From the (Windows based) Internet host:
# ping -6 2607:f140:400:1176:c466:2699:5ef1:d477 (to itself) # ping -6 2001:470:1f04:98e::1 (to the tunnel server) # ping -6 2001:470:1f04:98e::2 (to the OpenLbr)
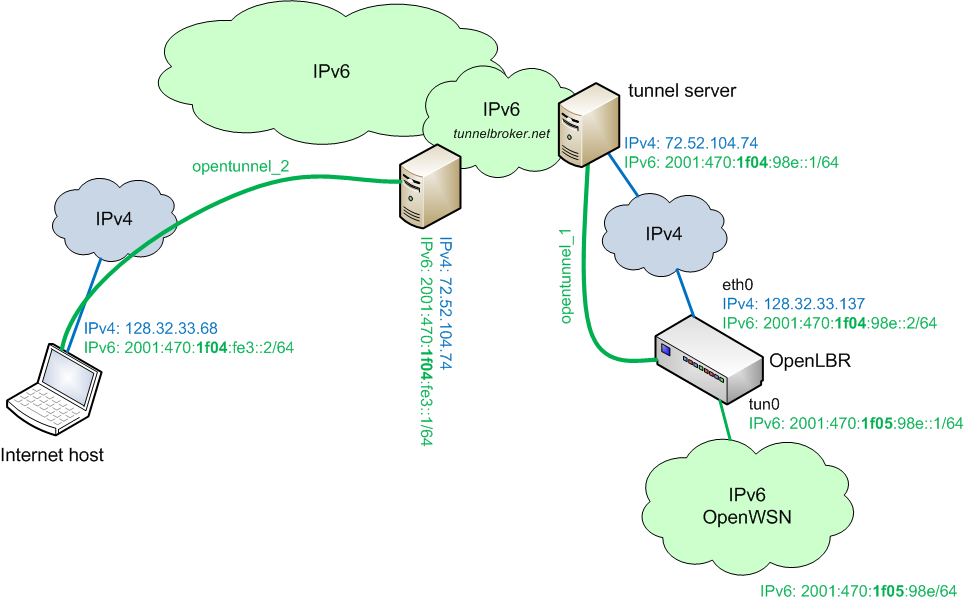
Setting up two tunnels using two public IPv4 addresses
If your Internet host does provide the Internet Host with an IPv6 address, it needs to tunnel into the IPv6 cloud to obtain one. You therefore can set up a second tunnel with http://tunnelbroker.net/ (with one account, you are allowed to set up up to 5 tunnel for free).
After registering your second tunnel, you can ask http://tunnelbroker.net/ to output the command you use to set it up. under Vista, it looks something like this:
netsh interface teredo set state disabled netsh interface ipv6 add v6v4tunnel opentunnel_2 128.32.33.68 72.52.104.74 netsh interface ipv6 add address opentunnel_2 2001:470:1f04:fe3::2 netsh interface ipv6 add route ::/0 opentunnel_2 2001:470:1f04:fe3::1 pause
You can save these lines in a file enable_opentunnel_2.bat. Then right click on it, and choose Run as administrator. The last line prevents the command window to close after the last command has been executed.
In command window, type
ipconfig /all
You should see opentunnel_2, which has appeared as a "virtual" interface:
Tunnel adapter opentunnel_2:
Connection-specific DNS Suffix . : EECS.Berkeley.EDU
Description . . . . . . . . . . . : Microsoft Direct Point-to-point Adapater
Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
IPv6 Address. . . . . . . . . . . : 2001:470:1f04:fe3::2(Preferred)
Link-local IPv6 Address . . . . . : fe80::9ccc:e411:7ac1:bbe1%41(Preferred)
Default Gateway . . . . . . . . . : 2001:470:1f04:fe3::1
DNS Servers . . . . . . . . . . . : 128.32.33.21
128.32.33.23
128.32.206.12
NetBIOS over Tcpip. . . . . . . . : Disabled
You can test your connection by pinging the different elements of your setup. A good practice is to ping from the closest element to the furthest, i.e.
- your local addresses:
ping 128.32.33.68,ping -6 2001:470:1f04:fe3::2 - the other endpoint of
opentunnel_2:ping 72.52.104.74,ping -6 2001:470:1f04:fe3::1 - the Internet-side of
opentunnel_1:ping 72.52.104.74,ping -6 2001:470:1f04:98e::1 - the OpenLBR-side of
opentunnel_1:ping 128.32.33.137,ping -6 2001:470:1f04:98e::2 - the OpenWSN side of your OpenLBR:
ping -6 2001:470:1f05:98e::1 - a mote in your OpenWSN network:
ping -6 2001:470:1f05:98e::4
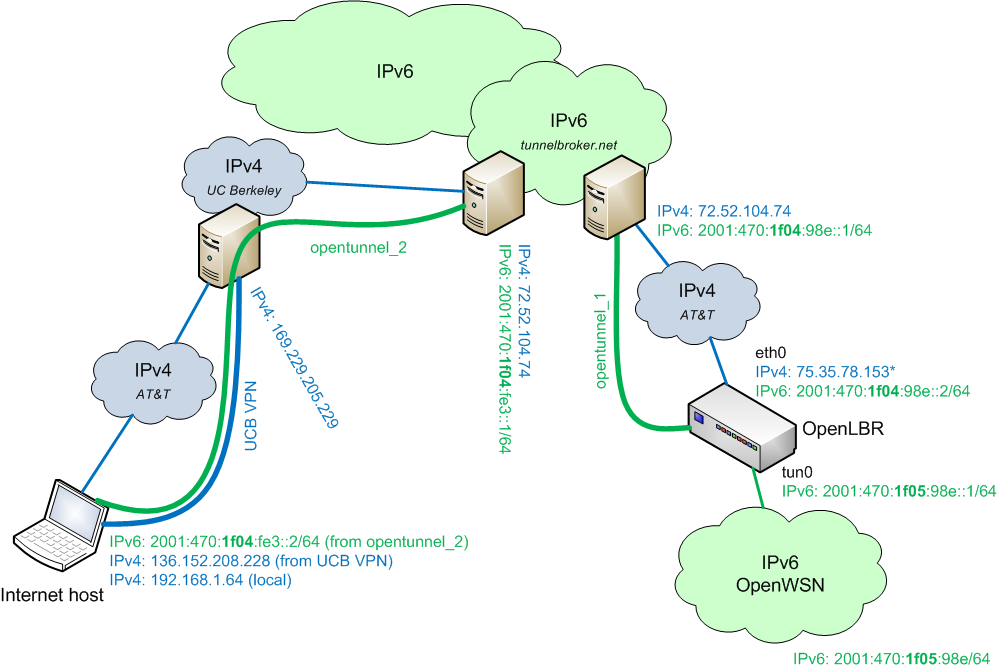
Setting up two tunnels using a single public IPv4 addresses
Note that the IPv4 endpoint of each tunnel needs to be a unique. This creates a problem if your Internet Host and OpenLBR share a same IPv4 public address through NAT (which is typical in a home environment). Below is a possible topology.
We assume that your OpenLBR has already set up a tunnel, using the procedure described above. To be able to set up a second tunnel from your Internet Host, you need to obtain a different public IPv4 address; you can do this using a VPN connection. In our case, we use the UC Berkeley VPN service, but any other service will do. Once you set up this IPv4 tunnel, use http://ip4.me to learn your public IPv4 address. Use that address as the IPv4 endpoint of your second http://tunnelbroker.net/ tunnel. You can set up opentunnel_2 using (in Vista):
netsh interface teredo set state disabled netsh interface ipv6 add v6v4tunnel IP6Tunnel 136.152.208.228 72.52.104.74 netsh interface ipv6 add address IP6Tunnel 2001:470:1f04:fe3::2 netsh interface ipv6 add route ::/0 IP6Tunnel 2001:470:1f04:fe3::1
Typing ipconfig /all lists all your interfaces:
your actual Ethernet interface with your private IP address (the one your router gave you)
Ethernet adapter Local Area Connection: Connection-specific DNS Suffix . : gateway.2wire.net Description . . . . . . . . . . . : Intel(R) 82566MM Gigabit Network Connection Physical Address. . . . . . . . . : 00-1D-72-96-0E-A0 DHCP Enabled. . . . . . . . . . . : Yes Autoconfiguration Enabled . . . . : Yes Link-local IPv6 Address . . . . . : fe80::a5fe:c55f:f05e:e299%10(Preferred) IPv4 Address. . . . . . . . . . . : 192.168.1.64(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.0 Lease Obtained. . . . . . . . . . : Tuesday, June 15, 2010 5:18:55 PM Lease Expires . . . . . . . . . . : Wednesday, June 16, 2010 5:18:54 PM Default Gateway . . . . . . . . . : 192.168.1.254 DHCP Server . . . . . . . . . . . : 192.168.1.254 DHCPv6 IAID . . . . . . . . . . . : 234888562 DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-10-1C-E7-1F-00-1D-72-96-0E-A0 DNS Servers . . . . . . . . . . . : 192.168.1.254 NetBIOS over Tcpip. . . . . . . . : Enabled
the virtual interface created by the IPv4 VPN tunnel called
UCB VPNin the diagram:Ethernet adapter Local Area Connection 3: Connection-specific DNS Suffix . : berkeley.edu Description . . . . . . . . . . . : Cisco AnyConnect VPN Virtual Miniport Adapter for Windows Physical Address. . . . . . . . . : 00-05-9A-3C-7A-00 DHCP Enabled. . . . . . . . . . . : No Autoconfiguration Enabled . . . . : Yes Link-local IPv6 Address . . . . . : fe80::ca1:b74:a951:9926%33(Preferred) IPv4 Address. . . . . . . . . . . : 136.152.208.228(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.254.0 Default Gateway . . . . . . . . . : 136.152.208.1 DHCPv6 IAID . . . . . . . . . . . : 318768538 DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-10-1C-E7-1F-00-1D-72-96-0E-A0 DNS Servers . . . . . . . . . . . : 128.32.136.12 128.32.206.9 NetBIOS over Tcpip. . . . . . . . : Enabledand the one created by the second
opentunnel_2tunnel:Tunnel adapter IP6Tunnel: Connection-specific DNS Suffix . : berkeley.edu Description . . . . . . . . . . . : Microsoft Direct Point-to-point Adapater Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0 DHCP Enabled. . . . . . . . . . . : No Autoconfiguration Enabled . . . . : Yes IPv6 Address. . . . . . . . . . . : 2001:470:1f04:fe3::2(Preferred) Link-local IPv6 Address . . . . . : fe80::2d3a:14ec:9ede:e516%42(Preferred) Default Gateway . . . . . . . . . : 2001:470:1f04:fe3::1 DNS Servers . . . . . . . . . . . : 128.32.136.12 128.32.206.9 NetBIOS over Tcpip. . . . . . . . : Disabled
You can test the connectivity by issuing a series on ping form the Internet host:
to its own addresses:
192.168.1.64,136.152.208.228and2001:470:1f04:fe3::2/64. The latter is shown below:C:\Windows\system32>ping -6 2001:470:1f04:fe3::2 Pinging 2001:470:1f04:fe3::2 from 2001:470:1f04:fe3::2 with 32 bytes of data: Reply from 2001:470:1f04:fe3::2: time<1ms Reply from 2001:470:1f04:fe3::2: time<1ms Reply from 2001:470:1f04:fe3::2: time<1ms Reply from 2001:470:1f04:fe3::2: time<1ms Ping statistics for 2001:470:1f04:fe3::2: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 0ms, Maximum = 0ms, Average = 0msto the IPv6 endpoint of the
opentunnel_2tunnel:C:\Windows\system32>ping -6 2001:470:1f04:fe3::1 Pinging 2001:470:1f04:fe3::1 from 2001:470:1f04:fe3::2 with 32 bytes of data: Reply from 2001:470:1f04:fe3::1: time=22ms Reply from 2001:470:1f04:fe3::1: time=22ms Reply from 2001:470:1f04:fe3::1: time=22ms Reply from 2001:470:1f04:fe3::1: time=23ms Ping statistics for 2001:470:1f04:fe3::1: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 22ms, Maximum = 23ms, Average = 22msto the IPv6 endpoint of the
opentunnel_1tunnel:C:\Windows\system32>ping -6 2001:470:1f04:98e::1 Pinging 2001:470:1f04:98e::1 from 2001:470:1f04:fe3::2 with 32 bytes of data: Reply from 2001:470:1f04:98e::1: time=22ms Reply from 2001:470:1f04:98e::1: time=22ms Reply from 2001:470:1f04:98e::1: time=22ms Reply from 2001:470:1f04:98e::1: time=22ms Ping statistics for 2001:470:1f04:98e::1: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 22ms, Maximum = 22ms, Average = 22msto the Internet-side IPv6 address of the OpenLBR
C:\Windows\system32>ping -6 2001:470:1f04:98e::2 Pinging 2001:470:1f04:98e::2 from 2001:470:1f04:fe3::2 with 32 bytes of data: Reply from 2001:470:1f04:98e::2: time=36ms Reply from 2001:470:1f04:98e::2: time=33ms Reply from 2001:470:1f04:98e::2: time=34ms Reply from 2001:470:1f04:98e::2: time=34ms Ping statistics for 2001:470:1f04:98e::2: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 33ms, Maximum = 36ms, Average = 34msto the OpenWSN-side IPv6 address of the OpenLBR
C:\Windows\system32>ping -6 2001:470:1f05:98e::1 Pinging 2001:470:1f05:98e::1 from 2001:470:1f04:fe3::2 with 32 bytes of data: Reply from 2001:470:1f05:98e::1: time=41ms Reply from 2001:470:1f05:98e::1: time=39ms Reply from 2001:470:1f05:98e::1: time=41ms Reply from 2001:470:1f05:98e::1: time=37ms Ping statistics for 2001:470:1f05:98e::1: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 37ms, Maximum = 41ms, Average = 39msto one of the wireless motes in the OpenWSN network:
C:\Windows\system32>ping -6 2001:470:1f05:98e::4 Pinging 2001:470:1f05:98e::4 from 2001:470:1f04:fe3::2 with 32 bytes of data: Reply from 2001:470:1f05:98e::4: time=548ms Reply from 2001:470:1f05:98e::4: time=611ms Reply from 2001:470:1f05:98e::4: time=588ms Reply from 2001:470:1f05:98e::4: time=592ms Ping statistics for 2001:470:1f05:98e::4: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 548ms, Maximum = 611ms, Average = 584ms
You can see how the average round-trip times increase. Note that you can test connectivity also from your OpenLBR, or from a mote in your OpenWSN network.
IPv6-in-IPv4Tunneling through an PPTP/VPN tunnel
You may want to establish the IPv6-in-IPv4 tunnel through a PPTP or VPN sessions for the following cases:
- When your OpenLBR connects from an IPv4 address which always changes (i.e. from a home). tunnelbroker.net now enables you to open the IPv6-in-IPv4 tunnel through a PPTP tunnel to their own servers.
- If your router does not allow IPv4 protocol 41 to go through. You can establish the IPv6-in-IPv4 tunnel through a VPN connection.
In the following example, we assume the latter case. We are using Cisco's AnyConnect to establish the VPN connection. The resulting interface is called cscotun0.
In case you are using a PPTP connection, simply replace cscotun0 by ppp0.
The following script opens the IPv6-in-IPv4 tunnel:
#!/bin/bash echo 'Make sure the VPN/PPTP tunnel is active!' addr=`ifconfig cscotun0 | sed -n '/inet addr:/s/.*addr:\([^ ]*\) .*/\1/p'` echo "Using address $addr" echo 'Configuring eth1' ifconfig eth1 10.0.0.2 netmask 255.0.0.0 ifconfig eth1 inet6 add 2001:470:846d:2::1/64 ifconfig eth1 up echo 'done.' echo 'Bringing up the IPv6-in-IPv4 tunnnel...' ifconfig sit0 up ifconfig sit0 inet6 tunnel ::72.52.104.74 ifconfig sit1 up ifconfig sit1 inet6 add 2001:470:1f04:1195::2/64 route -A inet6 add ::/0 dev sit1 echo 'done.' echo 'Configuring IP routing...' echo "1 admin" >> /etc/iproute2/rt_tables ip route add default dev cscotun0 table admin ip rule add from $addr table admin echo 'done.' echo 'Starting RADVD...' /etc/init.d/radvd start echo 'done.'
To close the tunnel:
#!/bin/bash addr=`ifconfig cscotun0 | sed -n '/inet addr:/s/.*addr:\([^ ]*\) .*/\1/p'` echo 'Stopping RADVD...' /etc/init.d/radvd stop echo 'done.' echo 'Ending IP routing...' ip rule del from $addr table admin ip route del default dev cscotun0 table admin sed "/1 admin/d" /etc/iproute2/rt_tables echo 'done.' echo 'Tearing down the IPv6-in-IPv4 tunnel...' route -A inet6 del ::/0 dev sit1 ifconfig sit1 down ifconfig sit0 down echo 'done.' echo 'Disabling eth1...' ifconfig eth1 del 2001:470:846d:2::1/64 ifconfig eth1 down echo 'done.' echo 'You can now close the VPN/PPTP tunnel.'
If everything works, go on to Use a Virtual Interface.