Interact over CoAP
This page is presented as a demo. Since it has no hardware dependency, you can easily replicate it on your computer.
This demo shows how easy it is to write an application to interact with an OpenWSN mote, from your computer, over CoAP. We will use the following:
- the firmware from the https://github.com/openwsn-berkeley/openwsn-fw repository, which we will emulate in the simulator (see OpenSim)
- the software from https://github.com/openwsn-berkeley/openwsn-sw repository
- the Python CoAP library from the https://github.com/openwsn-berkeley/coap repository
Setup
We start by cloning the 3 repositories side-by-side.
The next step is to build the firmware as a Python extension module so it can be simulated:
C:\Users\Thomas\Desktop\openwsn-fw>scons board=python toolchain=gcc oos_openwsn
scons: Reading SConscript files ...
___ _ _ _ ___ _ _
| . | ___ ___ ._ _ | | | |/ __>| \ |
| | || . \/ ._>| ' || | | |\__ \| |
`___'| _/\___.|_|_||__/_/ <___/|_\_|
|_| openwsn.org
[...]
scons: done building targets.
We can now start the OpenVisualizer application in simulation mode, with a web interface:
C:\Users\Thomas\Desktop\openwsn-sw\software\openvisualizer>scons runweb --sim --simCount=2
scons: Reading SConscript files ...
___ _ _ _ ___ _ _
| . | ___ ___ ._ _ | | | |/ __>| \ |
| | || . \/ ._>| ' || | | |\__ \| |
`___'| _/\___.|_|_||__/_/ <___/|_\_|
|_| openwsn.org
scons: done reading SConscript files.
scons: Building targets ...
Copy("bin\openVisualizerApp\sim_files", "..\..\..\openwsn-fw\firmware\openos\bsp\boards\python\openwsnmodule_obj.h")
Mkdir("bin\openVisualizerApp\sim_files\windows")
Copy("bin\openVisualizerApp\sim_files\windows\oos_openwsn-x86.pyd", "..\..\..\openwsn-fw\firmware\openos\projects\common
\oos_openwsn.pyd")
Copy("bin\openVisualizerApp\sim_files", "..\..\..\openwsn-fw\firmware\openos\projects\common\oos_openwsn.pyd")
Delete("build\runui\web_files")
Mkdir("C:\Users\Thomas\Desktop\openwsn-sw\software\openvisualizer\build\runui")
Copy("build\runui\web_files", "bin\openVisualizerApp\web_files")
Delete("build\runui\sim_files")
Mkdir("C:\Users\Thomas\Desktop\openwsn-sw\software\openvisualizer\build\runui")
Copy("build\runui\sim_files", "bin\openVisualizerApp\sim_files")
uiRunner(["bin\openVisualizerApp\openVisualizerWeb"], ["bin\openVisualizerApp\openVisualizerWeb.py"])
Child PID is 5460
scons: done building targets.
Open http://127.0.0.1:8080/ shows the web interface of the OpenVisualizer.
Interact with real mote
By default, cinfo,cwellknown applications are enabled in emulation mode, but not for real mote. If you want to try with real mote, you need
- Add the apps when compiling the code. E.g. scons board=openmote-cc2538 toolchain=armgcc apps=cinfo,cwellknown oos_openwsn
- Use the IP address of the node when accessing the application through Copper. E.g. bbbb::1415:92cc:0:2 is the IP address of emulated nodes.
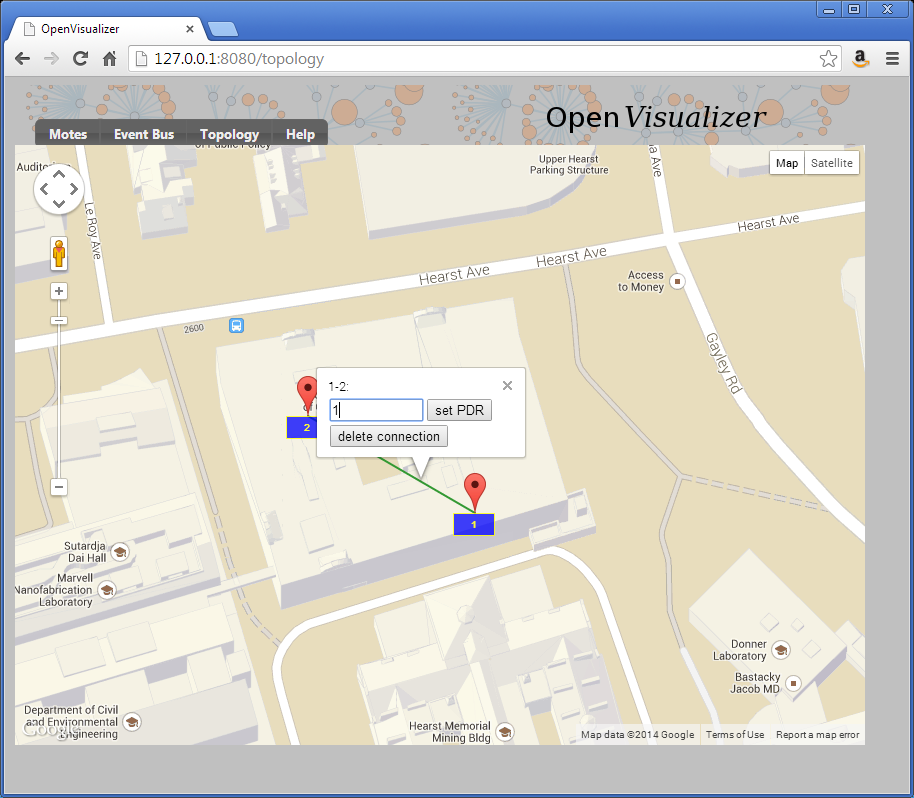
Edit the topology
Start by editing the topology so the two nodes are connected through a perfect wireless link (PDR=1).
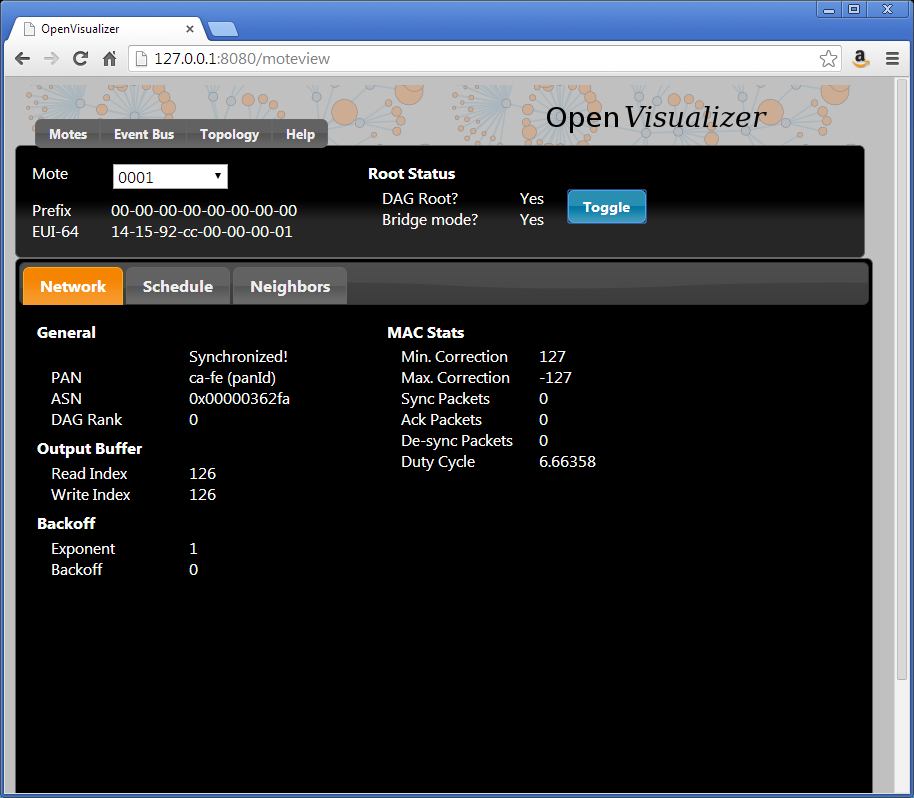
Start the network
You can now click the "Toggle" button so mote 1 becomes the DAGroot of the network. Mote 2 will synchronize to it, and RPL will set up the routing structure.
Ping a mote
To verify connectivity, you can ping mote 2
This page was put together using a Windows computer. If you're using Linux, everything is exactly the same, but you need to use command ping6 rather than ping.
C:\Users\Thomas>ping bbbb::1415:92cc:0:2
Pinging bbbb::1415:92cc:0:2 with 32 bytes of data:
Reply from bbbb::1415:92cc:0:2: time=50ms
Reply from bbbb::1415:92cc:0:2: time=67ms
Reply from bbbb::1415:92cc:0:2: time=65ms
Reply from bbbb::1415:92cc:0:2: time=59ms
Ping statistics for bbbb::1415:92cc:0:2:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 50ms, Maximum = 67ms, Average = 60ms
CoAP discovery
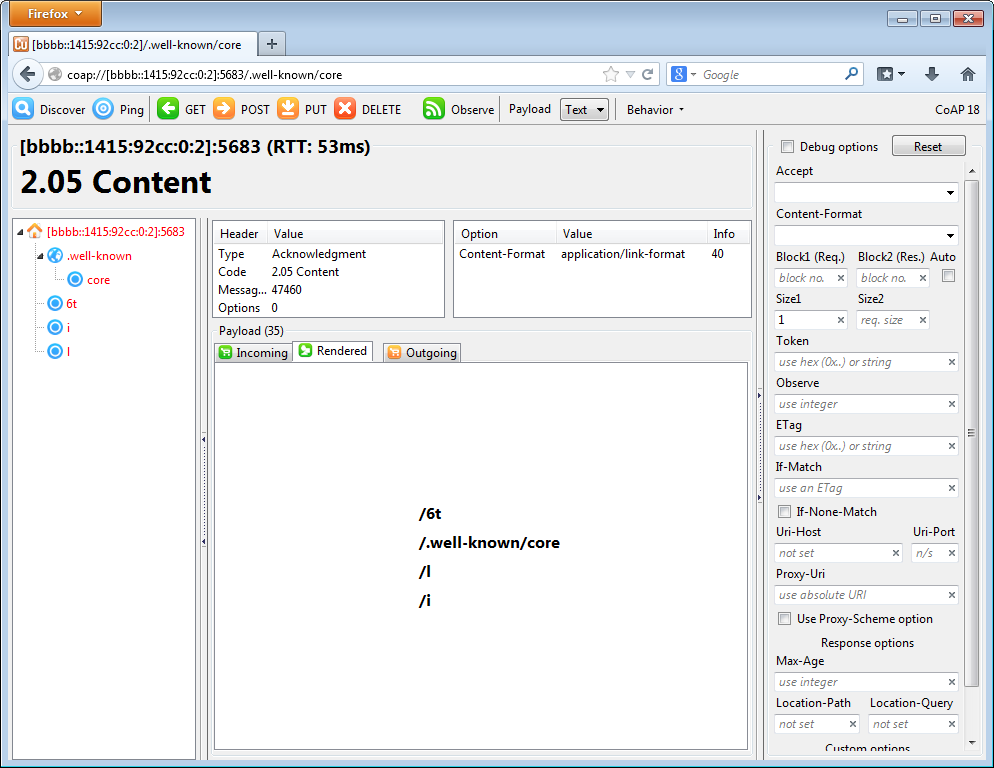
By default, mote 2 is a CoAP endpoint. To see the resources it has, you can install the Copper plugin for Firefox and navigate to the coap://[bbbb::1415:92cc:0:2]:5683/.well-known/core URI.
Alternatively, you can create a Python script which uses the Python CoAP module you just clones:
from coap import coap
c = coap.coap()
p = c.GET('coap://bbbb::1415:92cc:0:2/.well-known/core')
print ''.join([chr(b) for b in p])
Running is prints the same information
</6t>,</.well-known/core>,</l>,</i>
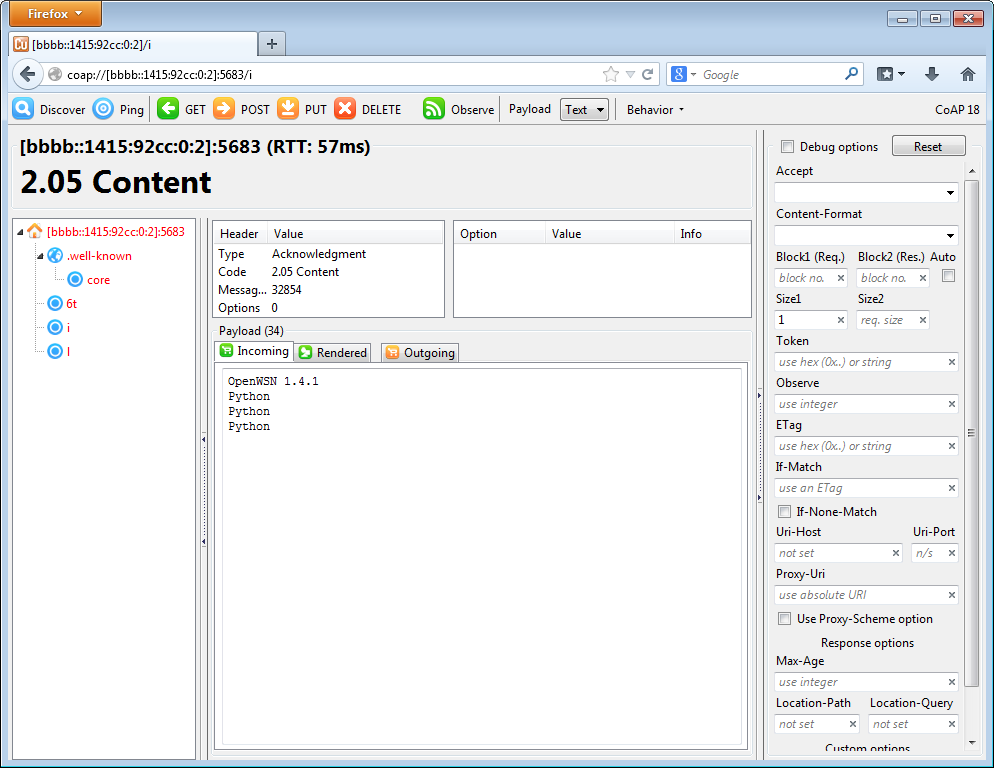
Getting information about the board
Doing a CoAP GET on /i resource gives you information about the board itself, including the firmware version, the micro-controller and radio used. Since the mote is emulation, it returns "Python" for latter.
Interact with an LED
You can also interact with the debug LED of the mote. This is done through the /l CoAP resource:
- a
GETindicates what state it is in - a
PUTallows you to set (1), clear (0) or toggle it (2)
The following script toggles the LED and verifies that its value has indeed changed:
from coap import coap
c = coap.coap()
p = c.GET('coap://[bbbb::1415:92cc:0:2]/l')
print chr(p[0])
c.PUT(
'coap://[bbbb::1415:92cc:0:2]/l',
payload = [ord('2')],
)
p = c.GET('coap://[bbbb::1415:92cc:0:2]/l')
print chr(p[0])
Running it shows that the LED was first OFF, then ON.
0 1
Next steps
Follow the Adding a CoAP app tutorial to add your own app.